Wij jitsi server: Difference between revisions
(→rules) |
(→rules6) |
||
| Line 140: | Line 140: | ||
==== rules6 ==== | ==== rules6 ==== | ||
#! /bin/bash | |||
# | |||
##### | |||
# | |||
# IPv6 rule file voor hobbynet-firewall | |||
# | |||
##### | |||
PUBIF="ens160" | |||
LOCIF="ens192" | |||
# include start rules | |||
. $WORK/in_start.ip6 | |||
# sta ssh toe van de Jitsi web/meet server interne interface | |||
$IP6TABLES -A INPUT -p tcp --dport 22 -s 2a02:968:ffff:999:172:31:1:54 -m conntrack --ctstate NEW -j ACCEPT | |||
# include default incoming rules UP | |||
. $WORK/in_up.ip6 | |||
# HTTP/HTTPS are always allowed: | |||
$IP6TABLES -A INPUT -p tcp --dport 80 -j ACCEPT | |||
$IP6TABLES -A INPUT -p tcp --dport 443 -j ACCEPT | |||
$IP6TABLES -A INPUT -p tcp --dport 4443 -j ACCEPT | |||
$IP6TABLES -A INPUT -p tcp --dport 4444 -j ACCEPT | |||
$IP6TABLES -A INPUT -p udp --dport 4446 -j ACCEPT | |||
$IP6TABLES -A INPUT -p tcp --dport 5222 -j ACCEPT | |||
$IP6TABLES -A INPUT -p tcp --dport 5269 -j ACCEPT | |||
$IP6TABLES -A INPUT -p tcp --dport 5280 -j ACCEPT | |||
$IP6TABLES -A INPUT -p tcp --dport 5281 -j ACCEPT | |||
$IP6TABLES -A INPUT -p tcp --dport 3478 -j ACCEPT | |||
$IP6TABLES -A INPUT -p udp --dport 3478 -j ACCEPT | |||
$IP6TABLES -A INPUT -p tcp --dport 5349 -j ACCEPT | |||
$IP6TABLES -A INPUT -p udp --dport 5349 -j ACCEPT | |||
$IP6TABLES -A INPUT -p tcp --dport 10000:90000 -j ACCEPT | |||
$IP6TABLES -A INPUT -p udp --dport 10000:90000 -j ACCEPT | |||
# Log alle uitgande TCP/UDP sessies sie stuk lopen | |||
$IP6TABLES -A INPUT -p tcp -j LOG --log-prefix "*Wrong Incoming tcp session-: " --log-level 7 | |||
$IP6TABLES -A INPUT -p udp -j LOG --log-prefix "*Wrong Incoming udp session-: " --log-level 7 | |||
# include default incoming rules DOWN | |||
. $WORK/in_down.ip6 | |||
## OUTPUT ## | |||
# include start rules | |||
. $WORK/out_start.ip6 | |||
# include default outgoing rules UP | |||
. $WORK/out_up.ip6 | |||
$IP6TABLES -A OUTPUT -p tcp --dport 80 -j ACCEPT -m iprange --dst-range '''2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57''' | |||
$IP6TABLES -A OUTPUT -p tcp --dport 443 -j ACCEPT -m iprange --dst-range '''2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57''' | |||
$IP6TABLES -A OUTPUT -p tcp --dport 4443 -j ACCEPT -m iprange --dst-range '''2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57''' | |||
$IP6TABLES -A OUTPUT -p tcp --dport 5222 -j ACCEPT -m iprange --dst-range '''2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57''' | |||
$IP6TABLES -A OUTPUT -p tcp --dport 5269 -j ACCEPT -m iprange --dst-range '''2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57''' | |||
$IP6TABLES -A OUTPUT -p tcp --dport 5280 -j ACCEPT -m iprange --dst-range '''2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57''' | |||
$IP6TABLES -A OUTPUT -p tcp --dport 5281 -j ACCEPT -m iprange --dst-range '''2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57''' | |||
$IP6TABLES -A OUTPUT -p tcp --dport 3478 -j ACCEPT -m iprange --dst-range '''2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57''' | |||
$IP6TABLES -A OUTPUT -p udp --dport 3478 -j ACCEPT -m iprange --dst-range '''2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57''' | |||
$IP6TABLES -A OUTPUT -p tcp --dport 5349 -j ACCEPT -m iprange --dst-range '''2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57''' | |||
$IP6TABLES -A OUTPUT -p udp --dport 5349 -j ACCEPT -m iprange --dst-range '''2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57''' | |||
$IP6TABLES -A OUTPUT -p tcp --dport 10000:90000 -j ACCEPT | |||
$IP6TABLES -A OUTPUT -p udp --dport 10000:90000 -j ACCEPT | |||
# sta uitgaand ssh toe naar de andere jitsi servers | |||
$IP6TABLES -A OUTPUT -p udp --dport 5349 -s '''2a02:968:ffff:999:172:31:1:54''' -j ACCEPT -m iprange --dst-range '''2a02:968:ffff:999:172:31:1:54-2a02:968:ffff:999:172:31:1:57''' | |||
#uitgaand mag http https | |||
$IP6TABLES -A OUTPUT -p tcp --dport 80 -j ACCEPT | |||
$IP6TABLES -A OUTPUT -p tcp --dport 443 -j ACCEPT | |||
# Log alle uitgande TCP/UDP sessies sie stuk lopen | |||
#$IP6TABLES -A OUTPUT -p tcp -j LOG --log-prefix "*Wrong Outgoing tcp sessione: " --log-level 7 | |||
#$IP6TABLES -A OUTPUT -p udp -j LOG --log-prefix "*Wrong Outgoing tcp sessionl: " --log-level 7 | |||
# include default outgoing rules down | |||
. $WORK/out_down.ip6 | |||
== frontend (meet server == | == frontend (meet server == | ||
Revision as of 20:57, 10 February 2022
doel
De server wij.hcc.nl verzorgt een jitsi server voor hcc
opzet
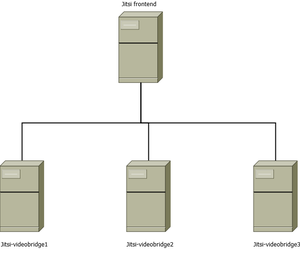
File:Jitsi diagram.dia De jitsi frontend fungeert als dirigent: hij bepaalt welke sessie op welke videobridge plaats vindt, hij is sessie broker. Elke videobridge handelt zijn eigen video verkeer af
Het cluster bestaat uit 4 servers
1. Frontend : deze is zeg maar de sessie broker 2,3,4. Videobridge 1 t/m 3: deze handelen al het video verkeer rechtstreeks af
installatie
Maak ssh-key aan op de meet/web server en verspreidt deze naar de video servers
alle servers
Voer op alle server het volgende uit:
apt install debconf-utils ca-certificates ca-certificates-java apt-transport-https apt-add-repository universe apt update apt full-upgrade -y curl https://download.jitsi.org/jitsi-key.gpg.key | sudo sh -c 'gpg --dearmor > /usr/share/keyrings/jitsi-keyring.gpg' echo 'deb [signed-by=/usr/share/keyrings/jitsi-keyring.gpg] https://download.jitsi.org stable/' | sudo tee /etc/apt/sources.list.d/jitsi-stable.list > /dev/null apt update
zorg er voor dat er CEPH share is naar het juiste certificaat
Nu bereiden we vast de configuratie voor voor op alle servers dit scheelt hoop apt vragen, vervang hier bij de vet gedrukte delen door de juiste hostnamen (let op FQDN) en het juiste pad naar het certificaat
cat << EOF | sudo debconf-set-selections jitsi-videobridge jitsi-videobridge/jvb-hostname string wij-test-web.hobby.nl jitsi-meet jitsi-meet/jvb-serve boolean false jitsi-meet-prosody jitsi-videobridge/jvb-hostname string wij-test-web.hobby.nl jitsi-meet-web-config jitsi-meet/cert-choice select I want to use my own certificate jitsi-meet-web-config jitsi-meet/cert-path-crt string /disk/site/etc/ssl/hobby.nl/hobby.nl.crt jitsi-meet-web-config jitsi-meet/cert-path-key string /disk/site/etc/ssl/hobby.nl/hobby.nl.key EOF
firewall
de servers moeten veel onderling communiseren daarom is belangrijk dat juiste poorten openstaan zelfde geld voor inkommende poorten pas de ip reeksen aan naar de juisten
rules
#! /bin/bash # ##### # # IPv4 rule file voor hobbynet-firewall # ##### PUBIF="ens160" LOCIF="ens192" # include start rules . $WORK/in_start.ip4 # sta ssh toe van de Jitsi web/meet server interne interface $IPTABLES -A INPUT -p tcp --dport 22 -s 172.31.1.54 -m conntrack --ctstate NEW -j ACCEPT # include default incoming rules UP . $WORK/in_up.ip4 # HTTP/HTTPS are always allowed: $IPTABLES -A INPUT -p tcp --dport 80 -m conntrack --ctstate NEW -j ACCEPT $IPTABLES -A INPUT -p tcp --dport 443 -m conntrack --ctstate NEW -j ACCEPT $IPTABLES -A INPUT -p tcp --dport 4443 -m conntrack --ctstate NEW -j ACCEPT $IPTABLES -A INPUT -p tcp --dport 4444 -m conntrack --ctstate NEW -j ACCEPT $IPTABLES -A INPUT -p udp --dport 4446 -j ACCEPT $IPTABLES -A INPUT -p tcp --dport 4096 -m conntrack --ctstate NEW -j ACCEPT $IPTABLES -A INPUT -p udp --dport 4096 -m conntrack --ctstate NEW -j ACCEPT $IPTABLES -A INPUT -p tcp --dport 5222 -m conntrack --ctstate NEW -j ACCEPT $IPTABLES -A INPUT -p tcp --dport 5269 -m conntrack --ctstate NEW -j ACCEPT $IPTABLES -A INPUT -p tcp --dport 5280 -m conntrack --ctstate NEW -j ACCEPT $IPTABLES -A INPUT -p tcp --dport 5281 -m conntrack --ctstate NEW -j ACCEPT $IPTABLES -A INPUT -p tcp --dport 3478 -m conntrack --ctstate NEW -j ACCEPT $IPTABLES -A INPUT -p udp --dport 3478 -j ACCEPT $IPTABLES -A INPUT -p tcp --dport 5349 -m conntrack --ctstate NEW -j ACCEPT $IPTABLES -A INPUT -p udp --dport 5349 -j ACCEPT $IPTABLES -A INPUT -p tcp --dport 10000:90000 -m conntrack --ctstate NEW -j ACCEPT $IPTABLES -A INPUT -p udp --dport 10000:90000 -j ACCEPT # Log alle uitgande TCP/UDP sessies sie stuk lopen $IPTABLES -A INPUT -p tcp -j LOG --log-prefix "*Wrong Incoming tcp sessionL: " --log-level 7 $IPTABLES -A INPUT -p udp -j LOG --log-prefix "*Wrong Incoming udp session : " --log-level 7 # include default incoming rules DOWN . $WORK/in_down.ip4 ## OUTPUT ## # include start rules . $WORK/out_start.ip4 # include default outgoing rules UP . $WORK/out_up.ip4 # include http_allow.ip4 #. $WORK/http_allow.ip4 # include ftp_allow.ip4 #. $WORK/ftp_allow.ip4 $IPTABLES -A OUTPUT -p tcp --dport 80 $IPTABLES -A OUTPUT -p tcp --dport 443 $IPTABLES -A OUTPUT -p tcp --dport 4443 -j ACCEPT -m iprange --dst-range 212.72.224.54-212.72.224.57 $IPTABLES -A OUTPUT -p tcp --dport 4096 $IPTABLES -A OUTPUT -p udp --dport 4096 $IPTABLES -A OUTPUT -p tcp --dport 5222 -j ACCEPT -d 127.0.0.1 $IPTABLES -A OUTPUT -p tcp --dport 5222 -j ACCEPT -d 127.0.1.1 $IPTABLES -A OUTPUT -p tcp --dport 5222 -j ACCEPT -m iprange --dst-range 212.72.224.54-212.72.224.57 $IPTABLES -A OUTPUT -p tcp --dport 5269 -j ACCEPT -m iprange --dst-range 212.72.224.54-212.72.224.57 $IPTABLES -A OUTPUT -p tcp --dport 5280 -j ACCEPT -m iprange --dst-range 212.72.224.54-212.72.224.57 $IPTABLES -A OUTPUT -p tcp --dport 5281 -j ACCEPT -m iprange --dst-range 212.72.224.54-212.72.224.57 $IPTABLES -A OUTPUT -p tcp --dport 3478 -j ACCEPT -m iprange --dst-range 212.72.224.54-212.72.224.57 $IPTABLES -A OUTPUT -p udp --dport 3478 -j ACCEPT -m iprange --dst-range 212.72.224.54-212.72.224.57 $IPTABLES -A OUTPUT -p tcp --dport 5349 -j ACCEPT -m iprange --dst-range 212.72.224.54-212.72.224.57 $IPTABLES -A OUTPUT -p udp --dport 5349 -j ACCEPT -m iprange --dst-range 212.72.224.54-212.72.224.57 $IPTABLES -A OUTPUT -p tcp --dport 10000:90000 -j ACCEPT $IPTABLES -A OUTPUT -p udp --dport 10000:90000 -j ACCEPT # uitgaand ssh mag naar de ander jitsi-servers vanaf de meet/web server $IPTABLES -A OUTPUT -p tcp --dport 22 -s 172.31.1.54 -j ACCEPT -m iprange --dst-range 172.31.1.54-172.31.1.57 #uitgaand mag http https $IPTABLES -A OUTPUT -p tcp --dport 80 -j ACCEPT $IPTABLES -A OUTPUT -p tcp --dport 443 -j ACCEPT # Log alle uitgande TCP/UDP sessies sie stuk lopen #$IPTABLES -A OUTPUT -p tcp -j LOG --log-prefix "*Wrong Outgoing tcp sessioni: " --log-level 7 #$IPTABLES -A OUTPUT -p udp -j LOG --log-prefix "*Wrong Outgoing tcp session : " --log-level 7 # include default outgoing rules down . $WORK/out_down.ip4
rules6
#! /bin/bash # ##### # # IPv6 rule file voor hobbynet-firewall # ##### PUBIF="ens160" LOCIF="ens192" # include start rules . $WORK/in_start.ip6 # sta ssh toe van de Jitsi web/meet server interne interface $IP6TABLES -A INPUT -p tcp --dport 22 -s 2a02:968:ffff:999:172:31:1:54 -m conntrack --ctstate NEW -j ACCEPT # include default incoming rules UP . $WORK/in_up.ip6 # HTTP/HTTPS are always allowed: $IP6TABLES -A INPUT -p tcp --dport 80 -j ACCEPT $IP6TABLES -A INPUT -p tcp --dport 443 -j ACCEPT $IP6TABLES -A INPUT -p tcp --dport 4443 -j ACCEPT $IP6TABLES -A INPUT -p tcp --dport 4444 -j ACCEPT $IP6TABLES -A INPUT -p udp --dport 4446 -j ACCEPT $IP6TABLES -A INPUT -p tcp --dport 5222 -j ACCEPT $IP6TABLES -A INPUT -p tcp --dport 5269 -j ACCEPT $IP6TABLES -A INPUT -p tcp --dport 5280 -j ACCEPT $IP6TABLES -A INPUT -p tcp --dport 5281 -j ACCEPT $IP6TABLES -A INPUT -p tcp --dport 3478 -j ACCEPT $IP6TABLES -A INPUT -p udp --dport 3478 -j ACCEPT $IP6TABLES -A INPUT -p tcp --dport 5349 -j ACCEPT $IP6TABLES -A INPUT -p udp --dport 5349 -j ACCEPT $IP6TABLES -A INPUT -p tcp --dport 10000:90000 -j ACCEPT $IP6TABLES -A INPUT -p udp --dport 10000:90000 -j ACCEPT # Log alle uitgande TCP/UDP sessies sie stuk lopen $IP6TABLES -A INPUT -p tcp -j LOG --log-prefix "*Wrong Incoming tcp session-: " --log-level 7 $IP6TABLES -A INPUT -p udp -j LOG --log-prefix "*Wrong Incoming udp session-: " --log-level 7 # include default incoming rules DOWN . $WORK/in_down.ip6 ## OUTPUT ## # include start rules . $WORK/out_start.ip6 # include default outgoing rules UP . $WORK/out_up.ip6 $IP6TABLES -A OUTPUT -p tcp --dport 80 -j ACCEPT -m iprange --dst-range 2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57 $IP6TABLES -A OUTPUT -p tcp --dport 443 -j ACCEPT -m iprange --dst-range 2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57 $IP6TABLES -A OUTPUT -p tcp --dport 4443 -j ACCEPT -m iprange --dst-range 2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57 $IP6TABLES -A OUTPUT -p tcp --dport 5222 -j ACCEPT -m iprange --dst-range 2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57 $IP6TABLES -A OUTPUT -p tcp --dport 5269 -j ACCEPT -m iprange --dst-range 2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57 $IP6TABLES -A OUTPUT -p tcp --dport 5280 -j ACCEPT -m iprange --dst-range 2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57 $IP6TABLES -A OUTPUT -p tcp --dport 5281 -j ACCEPT -m iprange --dst-range 2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57 $IP6TABLES -A OUTPUT -p tcp --dport 3478 -j ACCEPT -m iprange --dst-range 2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57 $IP6TABLES -A OUTPUT -p udp --dport 3478 -j ACCEPT -m iprange --dst-range 2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57 $IP6TABLES -A OUTPUT -p tcp --dport 5349 -j ACCEPT -m iprange --dst-range 2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57 $IP6TABLES -A OUTPUT -p udp --dport 5349 -j ACCEPT -m iprange --dst-range 2a02:968:1:2:212:72:224:54-2a02:968:1:2:212:72:224:57 $IP6TABLES -A OUTPUT -p tcp --dport 10000:90000 -j ACCEPT $IP6TABLES -A OUTPUT -p udp --dport 10000:90000 -j ACCEPT # sta uitgaand ssh toe naar de andere jitsi servers $IP6TABLES -A OUTPUT -p udp --dport 5349 -s 2a02:968:ffff:999:172:31:1:54 -j ACCEPT -m iprange --dst-range 2a02:968:ffff:999:172:31:1:54-2a02:968:ffff:999:172:31:1:57 #uitgaand mag http https $IP6TABLES -A OUTPUT -p tcp --dport 80 -j ACCEPT $IP6TABLES -A OUTPUT -p tcp --dport 443 -j ACCEPT # Log alle uitgande TCP/UDP sessies sie stuk lopen #$IP6TABLES -A OUTPUT -p tcp -j LOG --log-prefix "*Wrong Outgoing tcp sessione: " --log-level 7 #$IP6TABLES -A OUTPUT -p udp -j LOG --log-prefix "*Wrong Outgoing tcp sessionl: " --log-level 7 # include default outgoing rules down . $WORK/out_down.ip6
frontend (meet server
videobrige
update van jitsi
Nadat updates van jitsi zijn geweest moet het volgende script gedraaid worden
/usr/local/hobbynet/home/jitsi-images/update-jitsi.sh
Dit zorgt er voor dat het hcc logo etc etc wordt teruggezet, samen met nog wat settings.
update script jitsi-frontend
Bij apt upgrade/full-upgrade wordt automatisch door middel van een hook bepaalde settings goed gezet na de upgrade, dit gebeurt altijd, ook al is er geen jitsi update.
Het update script vindt je hier: /etc/apt/apt.conf.d/80upgradehook en ziet er als volgt uit:
DPkg::Post-Invoke {"/usr/local/hobbynet/local/jitsi/update-jitsi.sh";};
Het script wat hij aanroep is /usr/local/hobbynet/local/jitsi/update-jitsi.sh
#!/bin/bash echo "Jitsi frontend bijwerken" echo "plaats watermark" cp /usr/local/hobbynet/local/jitsi/Logo_hcc_RGB_png.png /usr/share/jitsi-meet/images/watermark.png echo "plaats favoicoonen" cp /usr/local/hobbynet/local/jitsi/favicon.ico /usr/share/jitsi-meet/images/favicon.ico cp /usr/local/hobbynet/local/jitsi/favicon.ico /usr/share/jitsi-meet/favicon.ico echo "backup oude interface config" cp /usr/share/jitsi-meet/interface_config.js /usr/local/hobbynet/local/jitsi/interface_config.js.old echo "vervang nodige variable in interface config, ipv oude config herbruiken" cat /usr/share/jitsi-meet/interface_config.js |sed "s/'Jitsi Meet'/'Wij HCC'/g"|sed "s/PROVIDER_NAME: 'Jitsi'/PROVIDER_NAME: 'Wij HCC'/g"|sed "s/'Jitsi Meet'/'Wij HCC'/g"|sed "s/DISABLE_JOIN_LEAVE_NOTIFICATIONS: false/DISABLE_JOIN_LEAVE_NOTIFICATIONS: true/g" >/usr/local/hobbynet/local/jitsi/interface_config.js.new echo "plaats nieuwe interface config" cp /usr/local/hobbynet/local/jitsi/interface_config.js.new /usr/share/jitsi-meet/interface_config.js
Het script plaatst het watermark en favicon op de juiste plek. Daarnaast doet hij de nodige aanpassingen in interface_config.js file met sed. Gebruik sed omdat er nog steeds nieuwe config opties bij komen en op deze manier gaan die niet verloren.
wanneer kan server herstart worden
cacti
Open cacti en kijk naar de statistieken en je ziet over wat actief is
cacti command line
voer het onderstaand script op cacti uit op cacti .
php /disk/site/hobbynet/cacti.hobby.nl/www/scripts/jitsi_get_total.php Bijeenkomsten:0 Deelnemers:5
Dit script laat alleen het aantal deelnemers zien niet aantal bijeenkomsten
accesslog op jitsi-frontend
kijk in /var/log/nginx/access.log en je ziet of er wat actief is je ziet alleen geen ip addressen hier in
truc op jitsi-frontend
Er is geen 'nette' manier om te zien hoeveel er van de server gebruik gemaakt wordt van af de command line op jitsi server
Maar er is wel een betrouwbare truc: kijk hoeveel sessies er naar TCP poort 443 ESTABLISHED zijn. (dit doe je op jitsi-frontend)
root@jitsi-frontend:~# netstat -an |grep ESTABLISHED | grep 443 tcp 0 0 212.72.224.120:443 94.213.158.57:55432 ESTABLISHED tcp 0 0 212.72.224.120:443 62.163.167.30:51728 ESTABLISHED tcp 0 0 212.72.224.120:443 178.84.60.147:61423 ESTABLISHED tcp 0 0 212.72.224.120:443 178.84.60.147:61432 ESTABLISHED tcp6 0 0 2a02:968:1:2:212:72:443 2001:981:97b8:1:2:62328 ESTABLISHED tcp6 0 0 2a02:968:1:2:212:72:443 2a02:a44e:56c8:1::62139 ESTABLISHED tcp6 0 0 2a02:968:1:2:212:72:443 2a02:a44f:39df:1::50801 ESTABLISHED